Are you sure you want to quit the chat?
In modern software development, security practices often involve securely managing and regularly updating cryptographic keys used for authentication and encryption. Azure Functions provides a powerful serverless computing platform that can be leveraged to automate tasks like key refreshing. In this article, we’ll demonstrate how to create an Azure Function in C# that retrieves public keys from a JWKS (JSON Web Key Set) endpoint and stores them securely in Azure Key Vault.
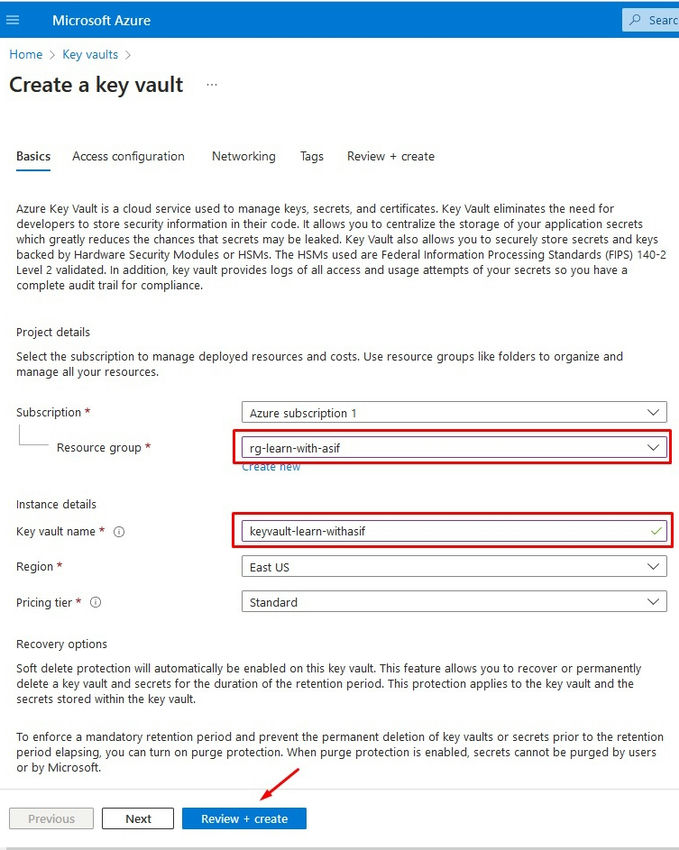
Before we start, make sure you have the following prerequisites set up.



Create a secret and put any random value in my case I have put the value asif123.


See the current version of the Secret.

Show the Secret Value

Copy Client ID & Tenant ID from your Registered App from Microsoft Entra ID.

Now go to the Web browser and place Tenant ID and Client ID to get the JWKS from Microsoft Entra ID.

We will create a C# Azure Function app that uses the HttpClient to fetch keys from a JWKS endpoint and then securely stores them in Azure Key Vault.
Create an Azure Function App in Azure Portal by following the steps.




Now Enabling Manage Identity on Azure Function App.




Create Azure Function from Visual Studio.

Copy the URL from browser

Copy the Key Vault URL

Create Azure Function in Visual Studio.

Go to the file and paste the copied URLs in highlighted places.

Run the Azure Function with F5 from Visual Studio in the Local environment and you can test it locally by signing in from Visual Studio to your Azure Portal.

Copy the URL and paste it into the Postman and execute this using Get request.


Copy the URL and paste it into the Postman and execute this using Get request.

you will get the message on the console as highlighted below.

Now go to the Azure portal go to the secret and click on it.

Now you can see that there are two versions of secret and secret points to the current version.

You can see the secret value that has a new value that was extracted from the JWKS URL.

Successfully refreshed the secret at Azure Key Vault from Azure Function that was locally executed using Managed Identity.
Summary:
This article outlines the process of automating key refreshing in Azure Functions using C# to securely manage and update cryptographic keys fetched from a JWKS (JSON Web Key Set) endpoint and store them in Azure Key Vault. The article emphasizes modern security practices in software development and the use of serverless computing for automation.
Overall, this summary encapsulates the process of implementing automated key refreshing in Azure Functions, highlighting best practices in security and Azure services integration for secure key management in cloud-based applications.
As part of the deduplication process, we also updated our reference table to reflect old-to-new key mappings. This allowed us to ensure that the correct GUIDs were assigned to the deduplicated records, maintaining the integrity of the data relationships in CRM.
At ITKnocks, we are more than an IT consulting company; we’re your strategic partner in business evolution. With a global footprint and a passion for technology, we craft innovative solutions, ensuring your success. Join us on a journey of excellence, where collaboration meets cutting-edge IT expertise.
